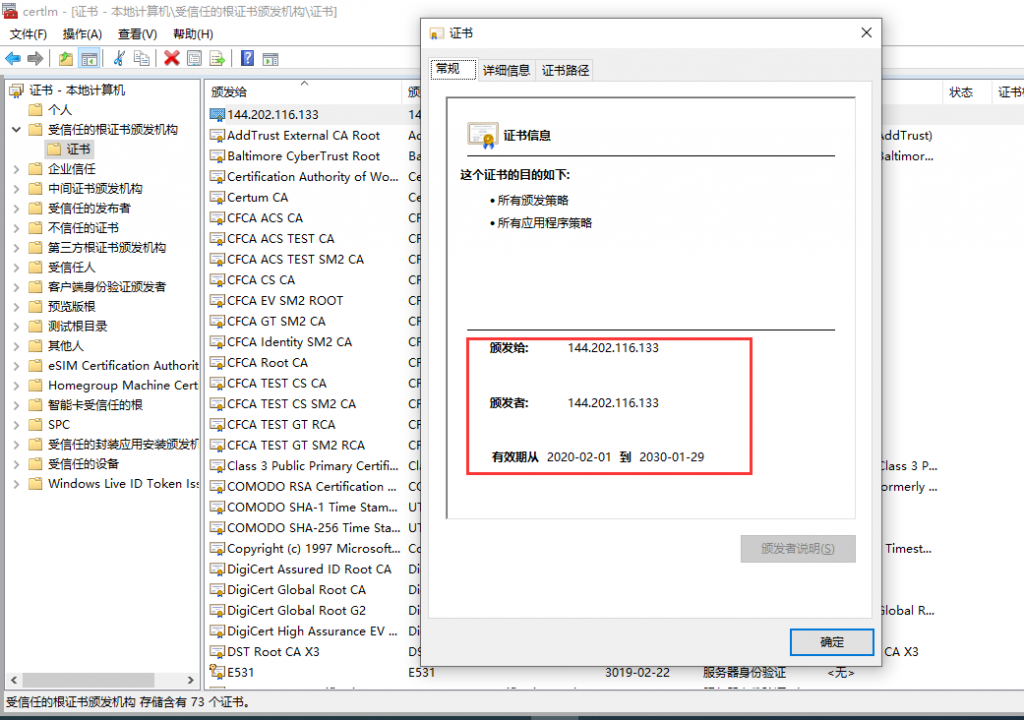
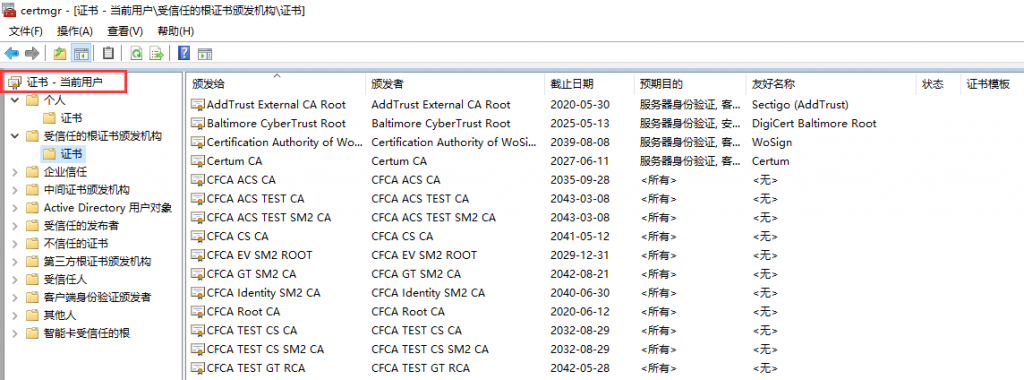
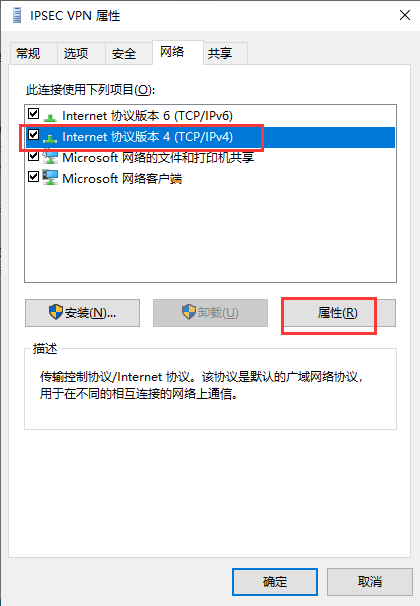
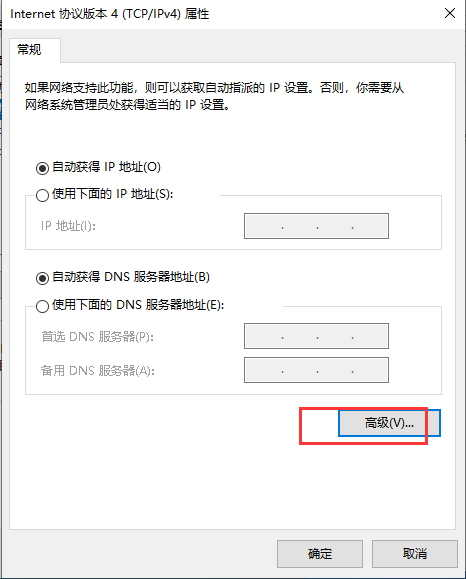
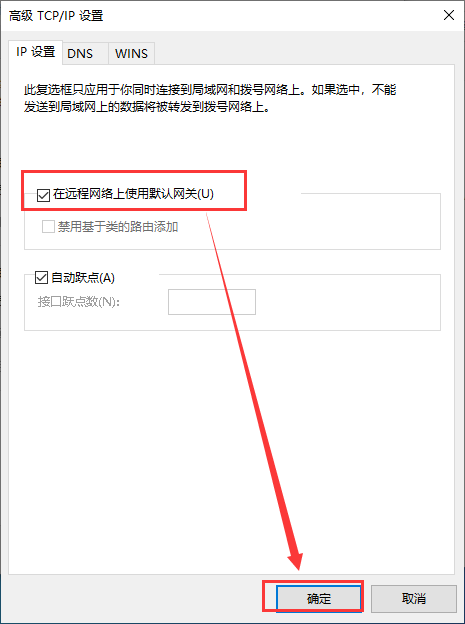
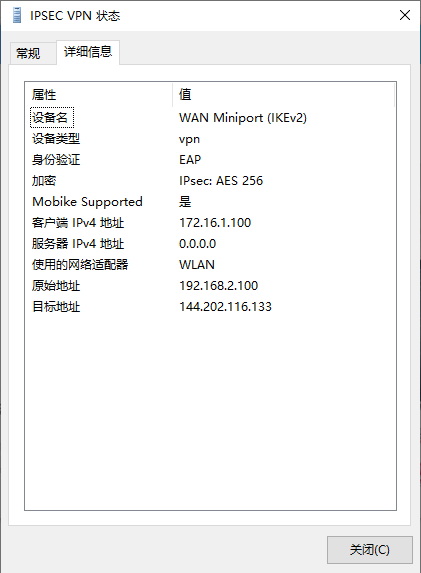
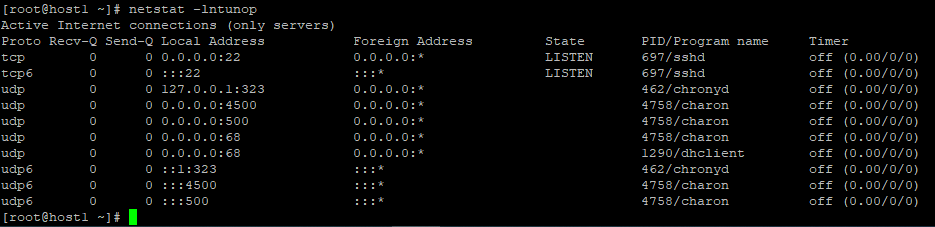
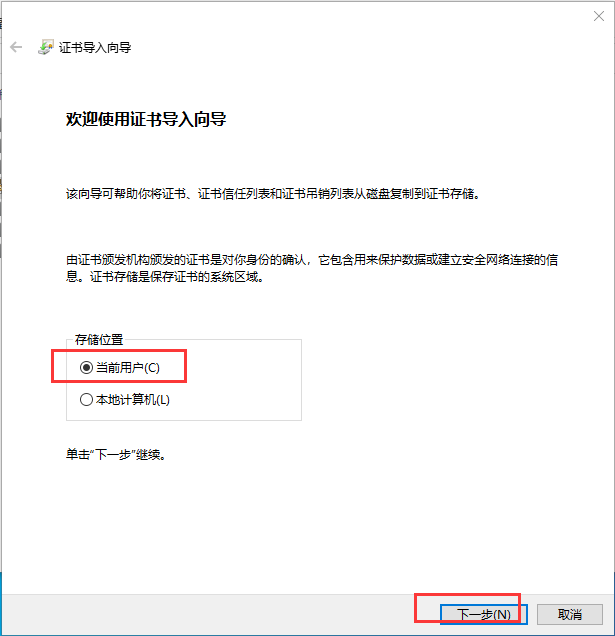
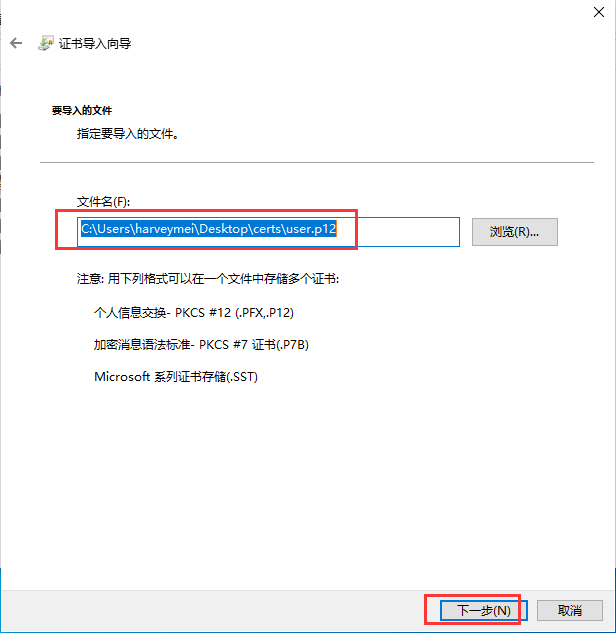
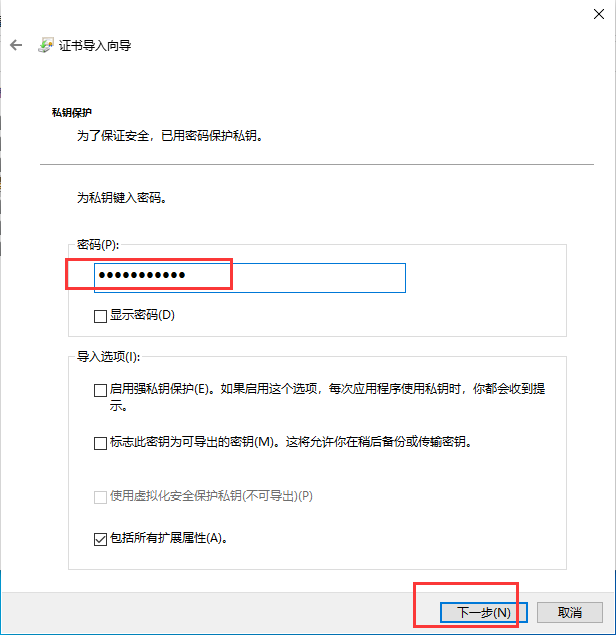
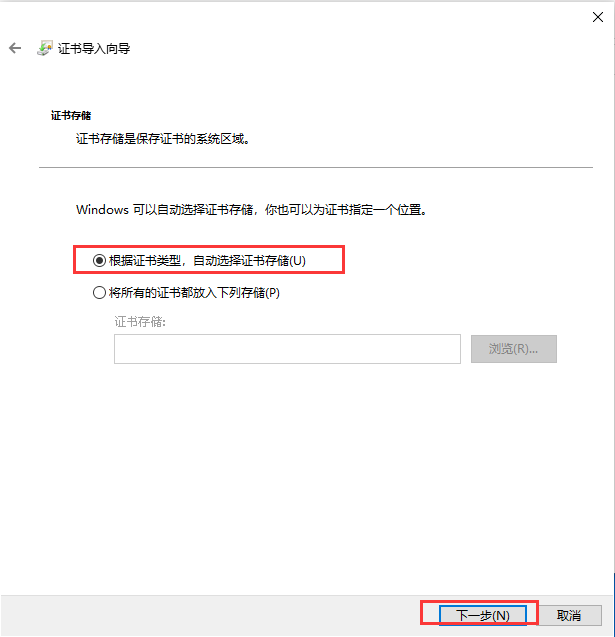
在三台主机上分别安装n2n并进行配置
host1:supernode/edge(192.168.172.1)
host2:edge(192.168.172.2)
host3:edge(192.168.172.3)
Community:linuxcache
Pre-Shared Key:5tgb6yhn7ujm
禁用防火墙
[root@host1 ~]# systemctl disable firewalld
Removed symlink /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service.
Removed symlink /etc/systemd/system/multi-user.target.wants/firewalld.service.
[root@host1 ~]# systemctl stop firewalld
[root@host1 ~]#
安装工具
[root@host1 ~]# yum -y install git gcc automake
下载源代码
https://github.com/ntop/n2n.git
[root@host1 ~]# git clone https://github.com/ntop/n2n.git
Cloning into 'n2n'...
remote: Enumerating objects: 1572, done.
remote: Total 1572 (delta 0), reused 0 (delta 0), pack-reused 1572
Receiving objects: 100% (1572/1572), 970.16 KiB | 0 bytes/s, done.
Resolving deltas: 100% (858/858), done.
[root@host1 ~]#
编译安装
[root@host1 ~]# cd n2n/
[root@host1 n2n]# ./autogen.sh
[root@host1 n2n]# ./configure
[root@host1 n2n]# make
[root@host1 n2n]# make PREFIX=/usr/local/n2n/ install
配置host1节点supernode服务脚本
[root@host1 ~]# vi /usr/lib/systemd/system/n2n_supernode.service
[Unit]
Description=n2n supernode
Wants=network-online.target
After=network-online.target
[Service]
ExecStart=/usr/local/n2n/sbin/supernode -l 1200
[Install]
WantedBy=multi-user.target
注册服务并启动服务
[root@host1 ~]# systemctl enable n2n_supernode
Created symlink from /etc/systemd/system/multi-user.target.wants/n2n_supernode.service to /usr/lib/systemd/system/n2n_supernode.service.
[root@host1 ~]# systemctl start n2n_supernode
[root@host1 ~]#
配置host1节点edge服务脚本
[root@host1 ~]# vi /usr/lib/systemd/system/n2n_edge.service
[Unit]
Description=n2n edge
Wants=network-online.target
After=network-online.target n2n_supernode.service
[Service]
ExecStart=/usr/local/n2n/sbin/edge -l localhost:1200 -c linuxcache -a 192.168.172.1 -k 5tgb6yhn7ujm -f
[Install]
WantedBy=multi-user.target
注册服务并启动服务
[root@host1 ~]# systemctl enable n2n_edge
Created symlink from /etc/systemd/system/multi-user.target.wants/n2n_edge.service to /usr/lib/systemd/system/n2n_edge.service.
[root@host1 ~]# systemctl start n2n_edge
[root@host1 ~]#
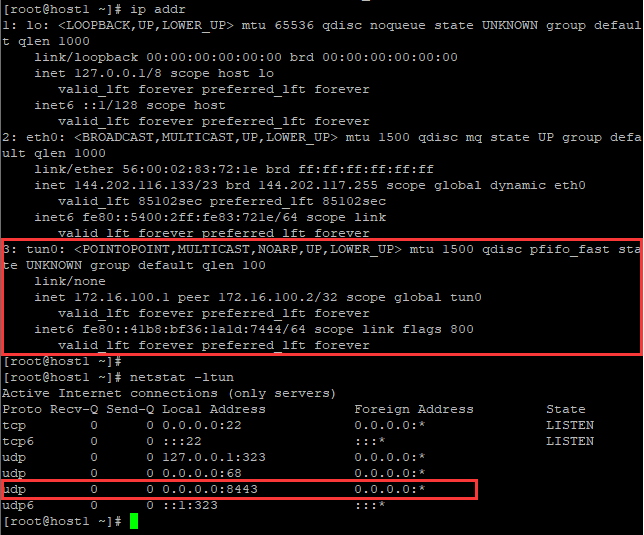
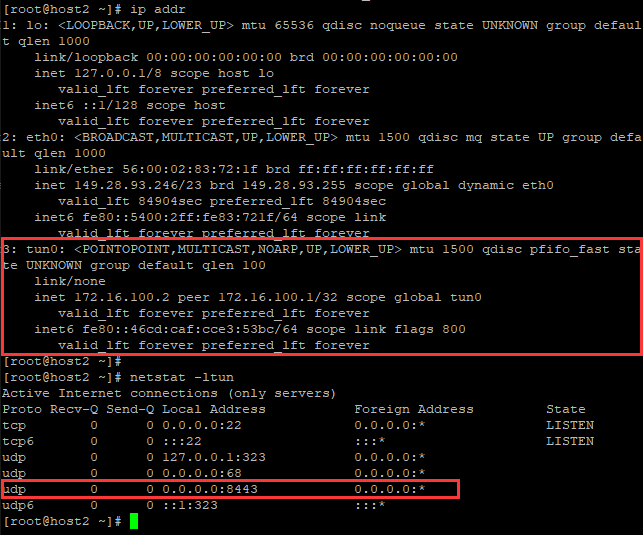
查看host1接口信息
[root@host1 ~]# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 56:00:02:83:72:1e brd ff:ff:ff:ff:ff:ff
inet 144.202.116.133/23 brd 144.202.117.255 scope global dynamic eth0
valid_lft 84884sec preferred_lft 84884sec
inet6 fe80::5400:2ff:fe83:721e/64 scope link
valid_lft forever preferred_lft forever
3: edge0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1290 qdisc pfifo_fast state UNKNOWN group default qlen 1000
link/ether de:23:7d:c9:85:e0 brd ff:ff:ff:ff:ff:ff
inet 192.168.172.1/24 brd 192.168.172.255 scope global edge0
valid_lft forever preferred_lft forever
inet6 fe80::dc23:7dff:fec9:85e0/64 scope link
valid_lft forever preferred_lft forever
[root@host1 ~]#
配置host2节点edge服务脚本
[root@host2 ~]# vi /usr/lib/systemd/system/n2n_edge.service
[Unit]
Description=n2n edge
Wants=network-online.target
After=network-online.target
[Service]
ExecStart=/usr/local/n2n/sbin/edge -l 144.202.116.133:1200 -c linuxcache -a 192.168.172.2 -k 5tgb6yhn7ujm -f
[Install]
WantedBy=multi-user.target
注册服务并启动服务
[root@host2 ~]# systemctl enable n2n_edge
Created symlink from /etc/systemd/system/multi-user.target.wants/n2n_edge.service to /usr/lib/systemd/system/n2n_edge.service.
[root@host2 ~]# systemctl start n2n_edge
[root@host2 ~]#
查看host2接口信息
[root@host2 ~]# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 56:00:02:83:72:1f brd ff:ff:ff:ff:ff:ff
inet 149.28.93.246/23 brd 149.28.93.255 scope global dynamic eth0
valid_lft 78885sec preferred_lft 78885sec
inet6 fe80::5400:2ff:fe83:721f/64 scope link
valid_lft forever preferred_lft forever
3: edge0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1290 qdisc pfifo_fast state UNKNOWN group default qlen 1000
link/ether ae:04:8c:77:da:be brd ff:ff:ff:ff:ff:ff
inet 192.168.172.2/24 brd 192.168.172.255 scope global edge0
valid_lft forever preferred_lft forever
inet6 fe80::ac04:8cff:fe77:dabe/64 scope link
valid_lft forever preferred_lft forever
[root@host2 ~]#
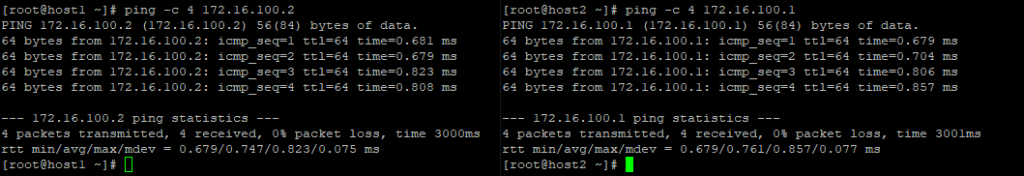
检测节点连通性(在host2主机上)
[root@host2 ~]# ping -c 4 192.168.172.1
PING 192.168.172.1 (192.168.172.1) 56(84) bytes of data.
64 bytes from 192.168.172.1: icmp_seq=1 ttl=64 time=0.877 ms
64 bytes from 192.168.172.1: icmp_seq=2 ttl=64 time=0.733 ms
64 bytes from 192.168.172.1: icmp_seq=3 ttl=64 time=0.844 ms
64 bytes from 192.168.172.1: icmp_seq=4 ttl=64 time=0.958 ms
--- 192.168.172.1 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3000ms
rtt min/avg/max/mdev = 0.733/0.853/0.958/0.080 ms
[root@host2 ~]#
配置host3节点edge服务脚本
[root@host3 ~]# vi /usr/lib/systemd/system/n2n_edge.service
[Unit]
Description=n2n edge
Wants=network-online.target
After=network-online.target
[Service]
ExecStart=/usr/local/n2n/sbin/edge -l 144.202.116.133:1200 -c linuxcache -a 192.168.172.3 -k 5tgb6yhn7ujm -f
[Install]
WantedBy=multi-user.target
注册服务并启动服务
[root@host3 n2n]# systemctl enable n2n_edge
Created symlink from /etc/systemd/system/multi-user.target.wants/n2n_edge.service to /usr/lib/systemd/system/n2n_edge.service.
[root@host3 n2n]# systemctl start n2n_edge
[root@host3 n2n]#
查看host3接口信息
[root@host3 ~]# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 56:00:02:83:80:03 brd ff:ff:ff:ff:ff:ff
inet 45.32.224.80/22 brd 45.32.227.255 scope global dynamic eth0
valid_lft 78416sec preferred_lft 78416sec
inet6 fe80::5400:2ff:fe83:8003/64 scope link
valid_lft forever preferred_lft forever
3: edge0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1290 qdisc pfifo_fast state UNKNOWN group default qlen 1000
link/ether d2:31:7d:96:46:41 brd ff:ff:ff:ff:ff:ff
inet 192.168.172.3/24 brd 192.168.172.255 scope global edge0
valid_lft forever preferred_lft forever
inet6 fe80::d031:7dff:fe96:4641/64 scope link
valid_lft forever preferred_lft forever
[root@host3 ~]#
检测节点连通性(在host3主机上)
[root@host3 ~]# ping -c 4 192.168.172.1
PING 192.168.172.1 (192.168.172.1) 56(84) bytes of data.
64 bytes from 192.168.172.1: icmp_seq=1 ttl=64 time=59.0 ms
64 bytes from 192.168.172.1: icmp_seq=2 ttl=64 time=25.9 ms
64 bytes from 192.168.172.1: icmp_seq=3 ttl=64 time=26.0 ms
64 bytes from 192.168.172.1: icmp_seq=4 ttl=64 time=27.2 ms
--- 192.168.172.1 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3003ms
rtt min/avg/max/mdev = 25.963/34.564/59.058/14.150 ms
[root@host3 ~]# ping -c 4 192.168.172.2
PING 192.168.172.2 (192.168.172.2) 56(84) bytes of data.
64 bytes from 192.168.172.2: icmp_seq=1 ttl=64 time=52.1 ms
64 bytes from 192.168.172.2: icmp_seq=2 ttl=64 time=26.0 ms
64 bytes from 192.168.172.2: icmp_seq=3 ttl=64 time=26.0 ms
64 bytes from 192.168.172.2: icmp_seq=4 ttl=64 time=25.9 ms
--- 192.168.172.2 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3003ms
rtt min/avg/max/mdev = 25.963/32.542/52.115/11.301 ms
[root@host3 ~]#
检测节点连通性(在host1主机上)
[root@host1 ~]# ping -c 4 192.168.172.2
PING 192.168.172.2 (192.168.172.2) 56(84) bytes of data.
64 bytes from 192.168.172.2: icmp_seq=1 ttl=64 time=1.43 ms
64 bytes from 192.168.172.2: icmp_seq=2 ttl=64 time=0.666 ms
64 bytes from 192.168.172.2: icmp_seq=3 ttl=64 time=0.840 ms
64 bytes from 192.168.172.2: icmp_seq=4 ttl=64 time=0.921 ms
--- 192.168.172.2 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3002ms
rtt min/avg/max/mdev = 0.666/0.964/1.432/0.287 ms
[root@host1 ~]# ping -c 4 192.168.172.3
PING 192.168.172.3 (192.168.172.3) 56(84) bytes of data.
64 bytes from 192.168.172.3: icmp_seq=1 ttl=64 time=33.4 ms
64 bytes from 192.168.172.3: icmp_seq=2 ttl=64 time=26.0 ms
64 bytes from 192.168.172.3: icmp_seq=3 ttl=64 time=26.3 ms
64 bytes from 192.168.172.3: icmp_seq=4 ttl=64 time=25.8 ms
--- 192.168.172.3 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3004ms
rtt min/avg/max/mdev = 25.859/27.923/33.456/3.202 ms
[root@host1 ~]#