基于OpenVPN使用预共享密钥加密的点到点VPN解决方案
安装依赖库EPEL及net-tools工具
[root@host1 ~]# yum -y install epel-release.noarch net-tools [root@host2 ~]# yum -y install epel-release.noarch net-tools
安装openvpn软件包
[root@host1 ~]# yum -y install openvpn [root@host2 ~]# yum -y install openvpn
配置防火墙,在两台主机开放UDP8443端口作为专用通信端口
[root@host1 ~]# firewall-cmd --permanent --add-port=8443/udp success [root@host1 ~]# firewall-cmd --reload success [root@host1 ~]# [root@host2 ~]# firewall-cmd --permanent --add-port=8443/udp success [root@host2 ~]# firewall-cmd --reload success [root@host2 ~]#
生成host1配置文件
[root@host1 ~]# vi /etc/openvpn/host1.conf proto udp mode p2p remote 149.28.93.246 rport 8443 local 0.0.0.0 lport 8443 dev-type tun tun-ipv6 resolv-retry infinite dev tun0 comp-lzo persist-key persist-tun cipher aes-256-cbc ifconfig 172.16.100.1 172.16.100.2 secret /etc/openvpn/p2p.key
生成预共享密钥文件并复制到host2主机相应目录
[root@host1 ~]# openvpn --genkey --secret /etc/openvpn/p2p.key [root@host1 ~]# cat /etc/openvpn/p2p.key # # 2048 bit OpenVPN static key # -----BEGIN OpenVPN Static key V1----- cb55061878ae55a026f04826c8c49669 efaa6a77d5077b0bff0d27eb7b0611de 849125952cfaea36f556c52b1a5725d2 69a79ec24526c363d636d64b9f9591e1 b64b5b20147d08e419c8e37b72320e52 4be7d1b23b0c76c21f950e611fafa25f a3811c610be55334b19f801cab1c31f3 f4bc5e5ff213b407b5c8321c0a619358 09e8dfb93561efebeff7f656d2dc7d7a 5c3ad585ccc81755fc711bcf7c702053 3a23335cdc3a2c372a0bdf18fb75cdd2 935ff0fe927e6f77e854cfb1547876d3 bc9df044f2a0cf9c88ba61b2b2731a04 16b1ad259d25f53d583cbcd0ed8a3c66 2c2b0ceb9115351760dfc42e1f2670d6 be49d22101387b08f9b54c0e23c11823 -----END OpenVPN Static key V1----- [root@host1 ~]#
生成host2配置文件
[root@host2 ~]# vi /etc/openvpn/hosts2.conf proto udp mode p2p remote 144.202.116.133 rport 8443 local 0.0.0.0 lport 8443 dev-type tun tun-ipv6 resolv-retry infinite dev tun0 comp-lzo persist-key persist-tun cipher aes-256-cbc ifconfig 172.16.100.2 172.16.100.1 secret /etc/openvpn/p2p.key [root@host2 ~]# vi /etc/openvpn/p2p.key # # 2048 bit OpenVPN static key # -----BEGIN OpenVPN Static key V1----- cb55061878ae55a026f04826c8c49669 efaa6a77d5077b0bff0d27eb7b0611de 849125952cfaea36f556c52b1a5725d2 69a79ec24526c363d636d64b9f9591e1 b64b5b20147d08e419c8e37b72320e52 4be7d1b23b0c76c21f950e611fafa25f a3811c610be55334b19f801cab1c31f3 f4bc5e5ff213b407b5c8321c0a619358 09e8dfb93561efebeff7f656d2dc7d7a 5c3ad585ccc81755fc711bcf7c702053 3a23335cdc3a2c372a0bdf18fb75cdd2 935ff0fe927e6f77e854cfb1547876d3 bc9df044f2a0cf9c88ba61b2b2731a04 16b1ad259d25f53d583cbcd0ed8a3c66 2c2b0ceb9115351760dfc42e1f2670d6 be49d22101387b08f9b54c0e23c11823 -----END OpenVPN Static key V1-----
启动host1上的OpenVPN服务并加载指定配置文件
[root@host1 ~]# nohup openvpn --config /etc/openvpn/host1.conf & [1] 1913 [root@host1 ~]# nohup: ignoring input and appending output to ‘nohup.out’ [root@host1 ~]# cat nohup.out Fri Jan 31 03:25:47 2020 Note: option tun-ipv6 is ignored because modern operating systems do not need special IPv6 tun handling anymore. Fri Jan 31 03:25:47 2020 disabling NCP mode (--ncp-disable) because not in P2MP client or server mode Fri Jan 31 03:25:47 2020 OpenVPN 2.4.8 x86_64-redhat-linux-gnu [Fedora EPEL patched] [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Nov 1 2019 Fri Jan 31 03:25:47 2020 library versions: OpenSSL 1.0.2k-fips 26 Jan 2017, LZO 2.06 Fri Jan 31 03:25:47 2020 TUN/TAP device tun0 opened Fri Jan 31 03:25:47 2020 /sbin/ip link set dev tun0 up mtu 1500 Fri Jan 31 03:25:47 2020 /sbin/ip addr add dev tun0 local 172.16.100.1 peer 172.16.100.2 Fri Jan 31 03:25:47 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]149.28.93.246:8443 Fri Jan 31 03:25:47 2020 UDP link local (bound): [AF_INET][undef]:8443 Fri Jan 31 03:25:47 2020 UDP link remote: [AF_INET]149.28.93.246:8443 [root@host1 ~]#
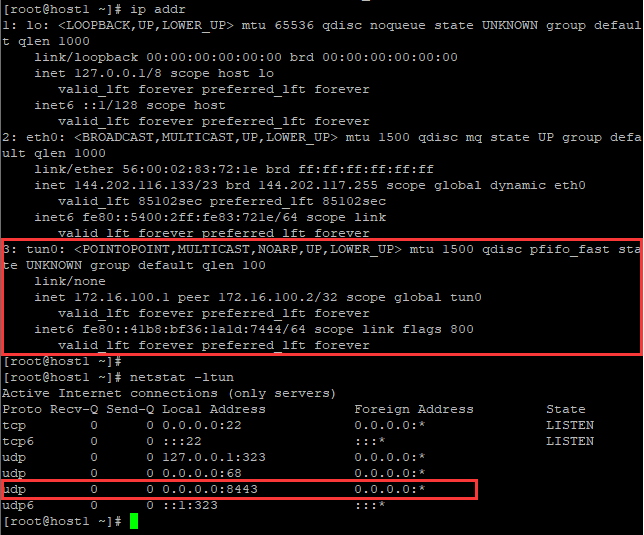
查看host1接口信息及端口监听信息
启动host2上的OpenVPN服务并加载指定配置文件
[root@host2 ~]# nohup openvpn --config /etc/openvpn/hosts2.conf & [1] 1741 [root@host2 ~]# nohup: ignoring input and appending output to ‘nohup.out’ [root@host2 ~]# cat nohup.out Fri Jan 31 03:28:03 2020 Note: option tun-ipv6 is ignored because modern operating systems do not need special IPv6 tun handling anymore. Fri Jan 31 03:28:03 2020 disabling NCP mode (--ncp-disable) because not in P2MP client or server mode Fri Jan 31 03:28:03 2020 WARNING: file '/etc/openvpn/p2p.key' is group or others accessible Fri Jan 31 03:28:03 2020 OpenVPN 2.4.8 x86_64-redhat-linux-gnu [Fedora EPEL patched] [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Nov 1 2019 Fri Jan 31 03:28:03 2020 library versions: OpenSSL 1.0.2k-fips 26 Jan 2017, LZO 2.06 Fri Jan 31 03:28:03 2020 TUN/TAP device tun0 opened Fri Jan 31 03:28:03 2020 /sbin/ip link set dev tun0 up mtu 1500 Fri Jan 31 03:28:03 2020 /sbin/ip addr add dev tun0 local 172.16.100.2 peer 172.16.100.1 Fri Jan 31 03:28:03 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]144.202.116.133:8443 Fri Jan 31 03:28:03 2020 UDP link local (bound): [AF_INET][undef]:8443 Fri Jan 31 03:28:03 2020 UDP link remote: [AF_INET]144.202.116.133:8443 [root@host2 ~]#
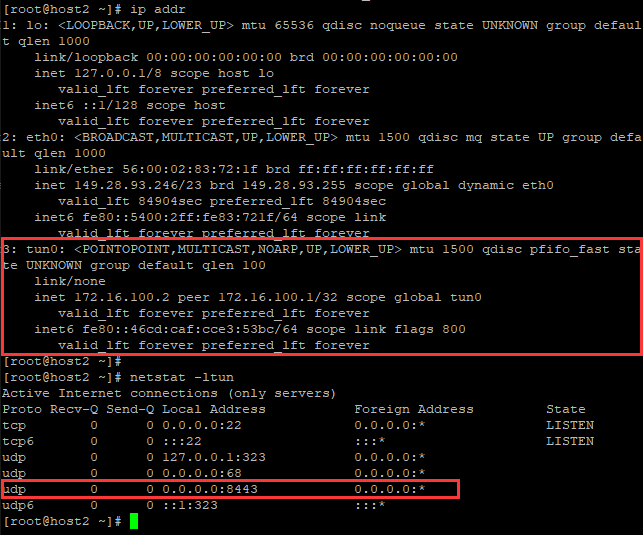
查看host2接口信息及端口监听信息
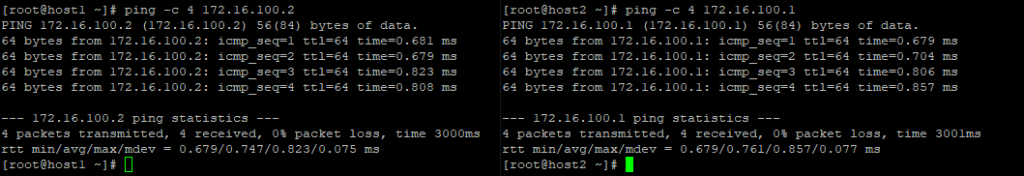
在两台主机上分别ping对端隧道IP地址