安装EPEL仓库源
[root@host1 ~]# yum -y install epel-release
更新缓存并安装StrongSwan及net-tools工具
[root@host1 ~]# yum makecache [root@host1 ~]# yum -y install strongswan net-tools
查看StrongSwan版本信息
[root@host1 ~]# yum info strongswan Loaded plugins: fastestmirror Loading mirror speeds from cached hostfile * base: repos-lax.psychz.net * epel: mirror.lax.genesisadaptive.com * extras: mirror.hostduplex.com * updates: repos-lax.psychz.net Installed Packages Name : strongswan Arch : x86_64 Version : 5.7.2 Release : 1.el7 Size : 4.0 M Repo : installed From repo : epel Summary : An OpenSource IPsec-based VPN and TNC solution URL : http://www.strongswan.org/ License : GPLv2+ Description : The strongSwan IPsec implementation supports both the IKEv1 and : IKEv2 key exchange protocols in conjunction with the native NETKEY : IPsec stack of the Linux kernel. [root@host1 ~]#
准备证书生成脚本
服务器证书脚本
[root@host1 ipsec.d]# cat server_key.sh #!/bin/bash if [ $1 ]; then CN=$1 echo "generating keys for $CN ..." else echo -e "usage:\n sh server_key.sh YOUR EXACT HOST NAME or SERVER IP\n Run this script in directory to store your keys" exit 1 fi mkdir -p private && mkdir -p cacerts && mkdir -p certs strongswan pki --gen --type rsa --size 4096 --outform pem > private/strongswanKey.pem strongswan pki --self --ca --lifetime 3650 --in private/strongswanKey.pem --type rsa --dn "C=HK, O=LINUXCACHE.COM, CN=$CN" --outform pem > cacerts/strongswanCert.pem echo 'CA certs at cacerts/strongswanCert.pem' strongswan pki --print --in cacerts/strongswanCert.pem sleep 1 echo "generating server keys ..." strongswan pki --gen --type rsa --size 2048 --outform pem > private/vpnHostKey.pem strongswan pki --pub --in private/vpnHostKey.pem --type rsa | \ strongswan pki --issue --lifetime 730 \ --cacert cacerts/strongswanCert.pem \ --cakey private/strongswanKey.pem \ --dn "C=HK, O=LINUXCACHE.COM, CN=$CN" \ --san $CN \ --flag serverAuth --flag ikeIntermediate \ --outform pem > certs/vpnHostCert.pem echo "vpn server cert at certs/vpnHostCert.pem" strongswan pki --print --in certs/vpnHostCert.pem [root@host1 ipsec.d]#
客户端证书脚本
[root@host1 ipsec.d]# cat client_key.sh #!/bin/bash info="usage:\n sh client_key.sh USER_NAME EMAIL \n Run this script in directory to store your keys" if [ $1 ]; then if [ $2 ]; then NAME=$1 MAIL=$2 echo "generating keys for $NAME $MAIL ..." else echo -e $info exit 1 fi else echo -e $info exit 1 fi mkdir -p private && mkdir -p cacerts && mkdir -p certs keyfile="private/"$NAME"Key.pem" certfile="certs/"$NAME"Cert.pem" p12file=$NAME".p12" strongswan pki --gen --type rsa --size 2048 \ --outform pem \ > $keyfile strongswan pki --pub --in $keyfile --type rsa | \ strongswan pki --issue --lifetime 730 \ --cacert cacerts/strongswanCert.pem \ --cakey private/strongswanKey.pem \ --dn "C=HK, O=LINUXCACHE.COM, CN=$MAIL" \ --san $MAIL \ --outform pem > $certfile strongswan pki --print --in $certfile echo "Enter password to protect p12 cert for $NAME" openssl pkcs12 -export -inkey $keyfile \ -in $certfile -name "$NAME's VPN Certificate" \ -certfile cacerts/strongswanCert.pem \ -caname "strongSwan Root CA" \ -out $p12file if [ $? -eq 0 ]; then echo "cert for $NAME at $p12file" fi [root@host1 ipsec.d]#
生成服务器证书
[root@host1 ipsec.d]# ./server_key.sh 144.202.116.133 generating keys for 144.202.116.133 ... CA certs at cacerts/strongswanCert.pem subject: "C=HK, O=LINUXCACHE.COM, CN=144.202.116.133" issuer: "C=HK, O=LINUXCACHE.COM, CN=144.202.116.133" validity: not before Feb 01 02:02:11 2020, ok not after Jan 29 02:02:11 2030, ok (expires in 3650 days) serial: 1d:40:6a:e0:af:56:64:33 flags: CA CRLSign self-signed subjkeyId: 91:38:53:8e:8e:85:aa:ec:db:75:1c:82:34:05:6c:7b:da:06:62:26 pubkey: RSA 4096 bits keyid: 7e:1e:66:62:f0:cc:d9:51:9e:ea:c0:97:37:d5:84:1c:b9:27:97:c2 subjkey: 91:38:53:8e:8e:85:aa:ec:db:75:1c:82:34:05:6c:7b:da:06:62:26 generating server keys ... vpn server cert at certs/vpnHostCert.pem subject: "C=HK, O=LINUXCACHE.COM, CN=144.202.116.133" issuer: "C=HK, O=LINUXCACHE.COM, CN=144.202.116.133" validity: not before Feb 01 02:02:13 2020, ok not after Jan 31 02:02:13 2022, ok (expires in 730 days) serial: 1d:ff:d1:51:97:c9:46:72 altNames: 144.202.116.133 flags: serverAuth ikeIntermediate authkeyId: 91:38:53:8e:8e:85:aa:ec:db:75:1c:82:34:05:6c:7b:da:06:62:26 subjkeyId: c8:82:e7:43:45:cf:0d:f1:8a:8b:7c:cc:ea:72:f0:4f:18:d9:85:fe pubkey: RSA 2048 bits keyid: 15:7d:c7:47:3e:07:7b:66:92:d0:2e:75:8e:78:0e:6b:72:8e:5e:b2 subjkey: c8:82:e7:43:45:cf:0d:f1:8a:8b:7c:cc:ea:72:f0:4f:18:d9:85:fe [root@host1 ipsec.d]#
生成客户端证书并为密钥对设置密码
[root@host1 ipsec.d]# ./client_key.sh harveymei harvey.mei@msn.com generating keys for harveymei harvey.mei@msn.com ... subject: "C=HK, O=LINUXCACHE.COM, CN=harvey.mei@msn.com" issuer: "C=HK, O=LINUXCACHE.COM, CN=144.202.116.133" validity: not before Feb 01 02:03:46 2020, ok not after Jan 31 02:03:46 2022, ok (expires in 730 days) serial: 60:f7:02:c5:33:21:3a:13 altNames: harvey.mei@msn.com flags: authkeyId: 91:38:53:8e:8e:85:aa:ec:db:75:1c:82:34:05:6c:7b:da:06:62:26 subjkeyId: ee:08:46:4e:bc:b1:7e:37:b5:b8:71:f1:5d:72:43:7f:4e:42:9c:40 pubkey: RSA 2048 bits keyid: 1a:8d:12:09:54:a6:a6:d4:f9:d4:7a:6c:75:0a:85:6d:90:b6:0d:fe subjkey: ee:08:46:4e:bc:b1:7e:37:b5:b8:71:f1:5d:72:43:7f:4e:42:9c:40 Enter password to protect p12 cert for harveymei Enter Export Password: Verifying - Enter Export Password: cert for harveymei at harveymei.p12 [root@host1 ipsec.d]#
复制客户端需要用到的证书
修改配置文件
修改ipsec.conf配置文件
初始配置文件
# ipsec.conf - strongSwan IPsec configuration file # basic configuration config setup # strictcrlpolicy=yes # uniqueids = no # Add connections here. # Sample VPN connections #conn sample-self-signed # leftsubnet=10.1.0.0/16 # leftcert=selfCert.der # leftsendcert=never # right=192.168.0.2 # rightsubnet=10.2.0.0/16 # rightcert=peerCert.der # auto=start #conn sample-with-ca-cert # leftsubnet=10.1.0.0/16 # leftcert=myCert.pem # right=192.168.0.2 # rightsubnet=10.2.0.0/16 # rightid="C=HK, O=Linux strongSwan CN=peer name" # auto=start
修改为
config setup uniqueids=never charondebug="cfg 2, dmn 2, ike 2, net 0" conn %default left=%defaultroute leftsubnet=0.0.0.0/0 leftcert=vpnHostCert.pem right=%any rightsourceip=172.16.1.100/16 conn CiscoIPSec keyexchange=ikev1 fragmentation=yes rightauth=pubkey rightauth2=xauth leftsendcert=always rekey=no auto=add conn XauthPsk keyexchange=ikev1 leftauth=psk rightauth=psk rightauth2=xauth auto=add conn IpsecIKEv2 keyexchange=ikev2 leftauth=pubkey rightauth=pubkey leftsendcert=always auto=add conn IpsecIKEv2-EAP keyexchange=ikev2 ike=aes256-sha1-modp1024! rekey=no leftauth=pubkey leftsendcert=always rightauth=eap-mschapv2 eap_identity=%any auto=add
修改strongswan.conf配置文件
初始配置文件
# strongswan.conf - strongSwan configuration file # # Refer to the strongswan.conf(5) manpage for details # # Configuration changes should be made in the included files charon { load_modular = yes plugins { include strongswan.d/charon/*.conf } } include strongswan.d/*.conf
修改为
charon { load_modular = yes duplicheck.enable = no compress = yes plugins { include strongswan.d/charon/*.conf } dns1 = 8.8.8.8 dns2 = 8.8.4.4 nbns1 = 8.8.8.8 nbns2 = 8.8.4.4 } include strongswan.d/*.conf
语法变化/错误的处理
Feb 01 02:41:00 host1 strongswan[4598]: /etc/strongswan/strongswan.conf:3: syntax error, unexpected ., expecting : or '{' or '=' [.]
charon { load_modular = yes duplicheck{ enable = no } compress = yes plugins { include strongswan.d/charon/*.conf } dns1 = 8.8.8.8 dns2 = 8.8.4.4 nbns1 = 8.8.8.8 nbns2 = 8.8.4.4 } include strongswan.d/*.conf
修改ipsec.secrets配置文件(账号密码)
初始配置文件
# ipsec.secrets - strongSwan IPsec secrets file
修改为
# ipsec.secrets - strongSwan IPsec secrets file : RSA vpnHostKey.pem : PSK "PSK_KEY" harveymei %any : EAP "harvey#pwd2020" harveymei %any : XAUTH "harvey#pwd2020"
开启内核及防火墙包转发设置
内核
[root@host1 strongswan]# echo "net.ipv4.ip_forward=1" >> /etc/sysctl.conf [root@host1 strongswan]# sysctl -p net.ipv6.conf.all.accept_ra = 2 net.ipv6.conf.eth0.accept_ra = 2 net.ipv4.ip_forward = 1 [root@host1 strongswan]#
防火墙
[root@host1 ~]# firewall-cmd --list-all public (active) target: default icmp-block-inversion: no interfaces: eth0 sources: services: dhcpv6-client ssh ports: protocols: masquerade: no forward-ports: source-ports: icmp-blocks: rich rules: [root@host1 ~]# firewall-cmd --permanent --add-service=ipsec success [root@host1 ~]# firewall-cmd --permanent --add-port=4500/udp success [root@host1 ~]# firewall-cmd --permanent --add-masquerade success [root@host1 ~]# firewall-cmd --reload success [root@host1 ~]# firewall-cmd --list-all public (active) target: default icmp-block-inversion: no interfaces: eth0 sources: services: dhcpv6-client ipsec ssh ports: 4500/udp protocols: masquerade: yes forward-ports: source-ports: icmp-blocks: rich rules: [root@host1 ~]#
启动服务
[root@host1 ~]# systemctl enable strongswan Created symlink from /etc/systemd/system/multi-user.target.wants/strongswan.service to /usr/lib/systemd/system/strongswan.service. [root@host1 ~]# systemctl start strongswan
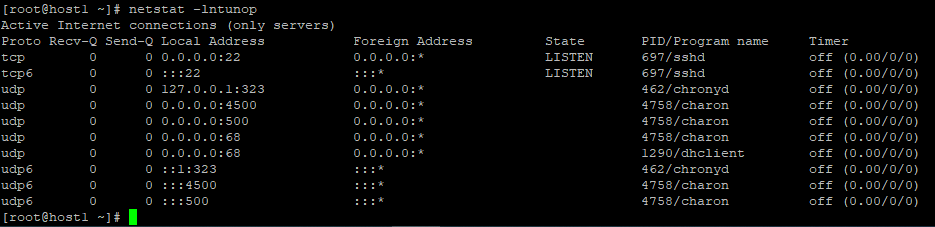
查看端口监听